Layer 5 - Monitor/Audit
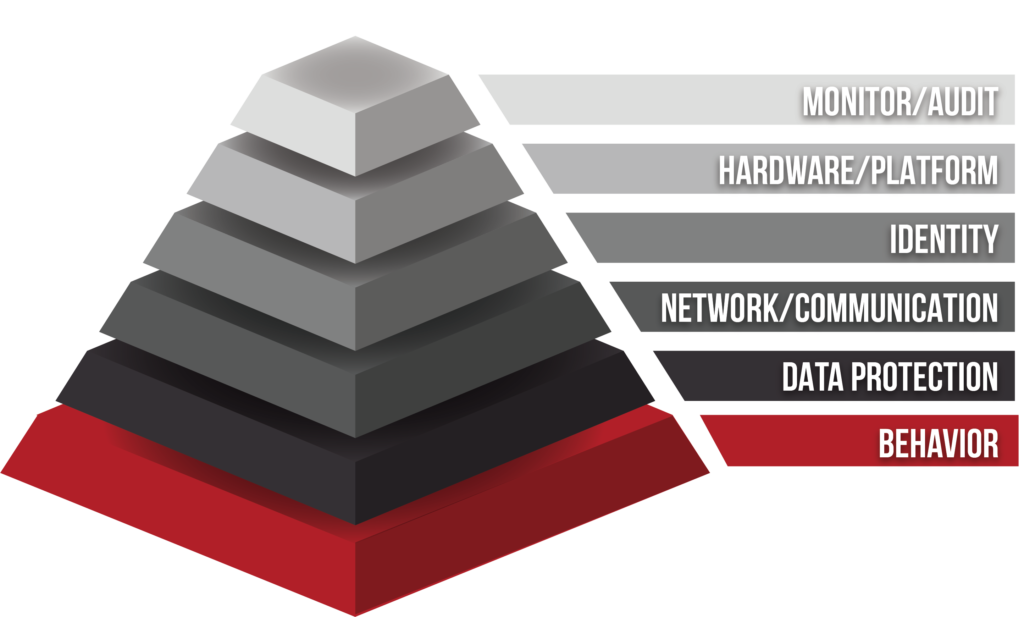
More About Level 5 - Monitor/AUDIT
Let’s discuss Layer 5. This is the layer where you will be monitoring and auditing your network and possibly blocking websites or suspicious emails. When you begin auditing and monitoring your network, you will find things that alarm you, so you must make tweaks and changes to your network and to your cybersecurity hygiene.
Once you have monitored and audited your network, you may decide that there are things you want to block. I think it’s appropriate to do that, but you must remember that your family is different than your company. You can go into your company and tell your staff what will be blocked because you pay them. You can say, “During these eight hours, these are the things you can and cannot do on the technology that we provide for you.”
However, when you’re dealing for family, how are you going to audit them? How’s that going to go over? What’s their reaction going to be? Despite the backlash, we think blocking is important, and there are some great technologies out there to help with that.
If you’re a family trying to control content for your kids online, try Circle Home Plus, formerly known as Disney Circle. It’s a great technology. If you prefer something else, go get it and implement it.
For the best protection, use a commercial grade product, such as Zsclaer. It costs more, but it’s a better product, especially for individuals who are targeted.
As you block content, there will be ramifications from your family. You need to think about that, and I would really encourage you to have that conversation about cybersecurity hygiene with your family, which is a concept we discussed in Layer Zero.
You have to establish acceptable ranges of behavior. Every family’s going to be a little bit different because families may have different views about acceptable levels of behavior, especially concerning topics such as violence and mature content. For example, we don’t want bomb making in our family. However, there could be a family that doesn’t believe that bomb making is a big deal because they live on a farm, and they want to blow up a tree stump.
Different families will have different levels of acceptable content, so I encourage you to think about what is acceptable before you just dive in and start blocking content. Besides blocking content, you still have to monitor and audit internet usage on a regular basis. Monitoring and auditing can also alert you to a threat actor who is trying to infiltrate your network and cause harm.
Although monitoring and auditing is extremely important, a lot of times families don’t have the bandwidth to do this. They have too much going on, so they want to pay a professional to monitor, audit, and block for them. This is an area where you might need to pay a professional to help you on a regular basis because the sooner you can catch a threat actor, the sooner you can take action. Sometimes you might find someone trying to take over your email account, or sometimes you might find someone who is bullying your child online. You can catch that early with regular monitoring and auditing, and in some cases, you can even prevent your system from being compromised.
When threat actors infiltrate your network or they are in your computers, they often remain there for months. They take their time, so they get the juiciest information. If you monitor and audit regularly, you’re going to find them more quickly, and you may not be as compromised. So, this is just one more reason to use professional help. There’s a lot more we talk about, so please sign up for a workshop and check out the material on our website. We look forward to helping you protect your family and your future.
