Layer 0 - Behavior
More About Level 0 - Behavior
Let’s discuss layer zero of cybersecurity. We call this layer zero because it’s the very first place you need to start. We also call it layer zero to draw your attention to the fact that in layer zero it’s all about the behavior, and we, as cybersecurity experts, can’t necessarily control your behavior.
In reality, we have zero control. We can make some recommendations and educate you, but at the end of the day, your behavior is really up to you.
We also call this layer security hygiene. When you hear cybersecurity professionals ask, “What’s your cybersecurity hygiene,” what they’re really asking is, “How are you acting online? What are you doing? What websites and apps are you interacting with, and where are you going?”
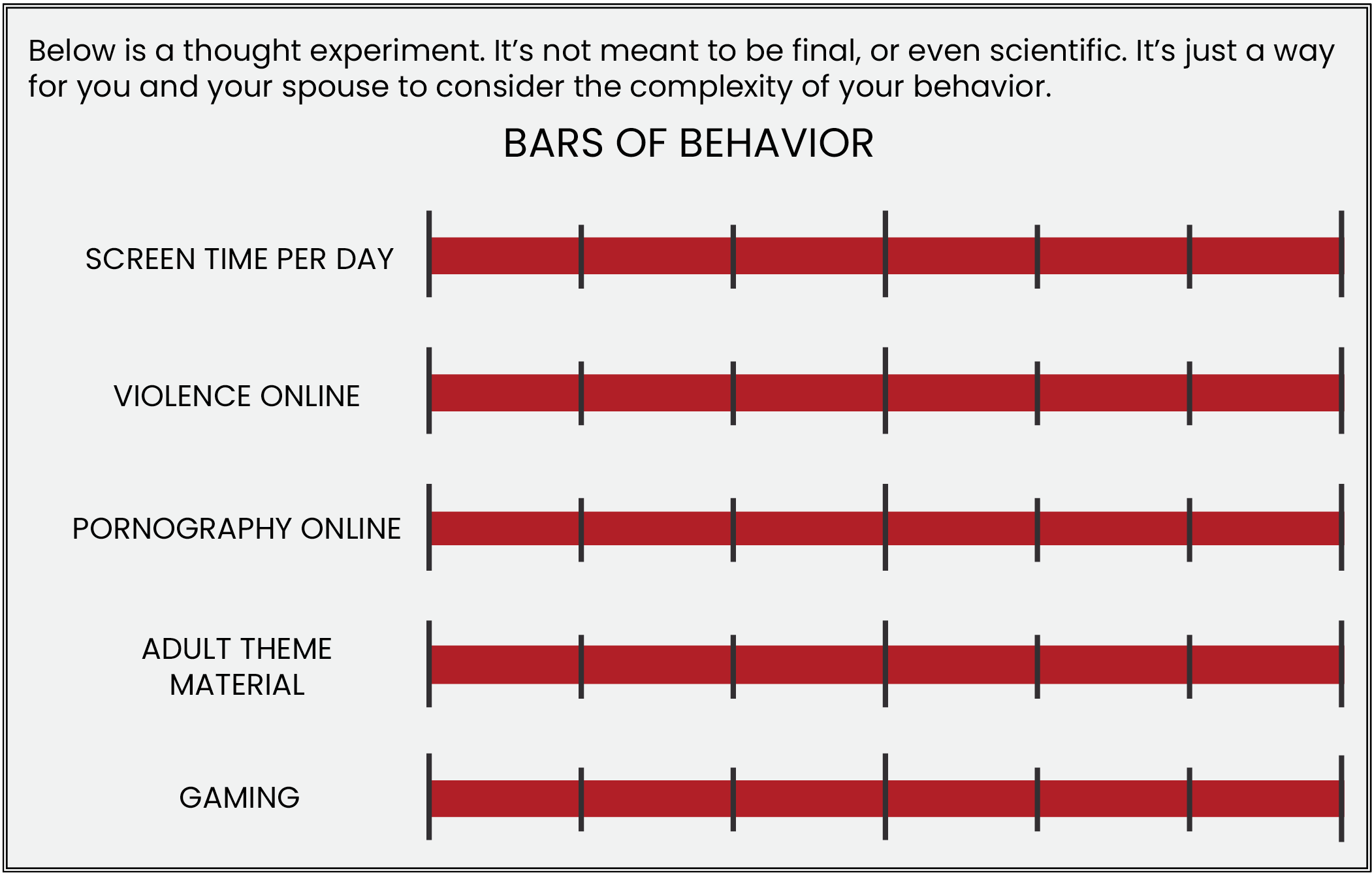
We chose to name the first layer “behavior” because we feel the term is a good way to describe cybersecurity hygiene. When it comes to behavior, you must have a talk with your spouse and your children to determine what types of behavior are appropriate for your family.
We recommend that you build trust with your children before having “the talk” with them about their behavior on the internet. How can you build that foundation of respect with your kids so that you can have this discussion? We have tools to help you have this conversation in our workbook. I promise you we can help you be a secure family, and you’ll be a lot happier when you have better cybersecurity. Your family may have challenges with digital solutions or screen time, but having a good discussion about online behavior can improve your family’s cybersecurity.
One of the questions you have to work out with your spouse/partner is:
- What is acceptable behavior for your children?
- What will we allow and what will we not allow?
- What’s acceptable content?
- What are acceptable apps?
- What’s acceptable screen time?
- What’s acceptable gaming time?
- What’s the acceptable number of, of devices someone can own or have?