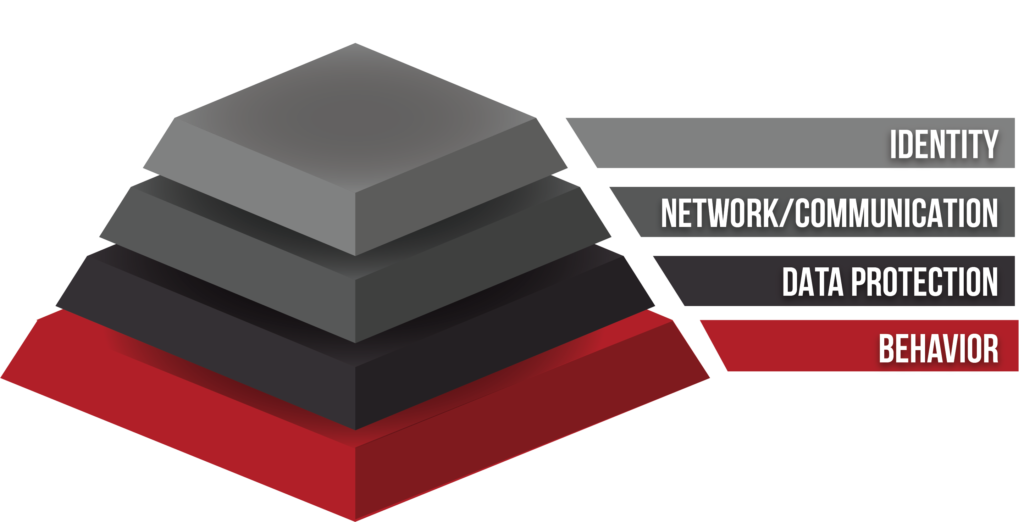
Layer 3 - Identity
More About Level 3 - IDENTITY
Let’s discuss Layer 3 — Identity. This is the new frontier in cybersecurity. You might be maintaining a lot of identities in the digital world. Perhaps you’ve got an identity for your Starbucks account and another identity for your car wash. You’ve got all these usernames and passwords associated with multiple accounts. You’ve also got your email, where they send password resets to. You probably have a lot of technology you’re dealing with right now, and it’s all centered around your online identity. With all this information floating around online about you, cybersecurity has become a really important part of your life. In order to protect yourself and your online identity, it’s important to use multifactor authentication and a password management software, such as 1Password.
In the past it was hard for threat actors to steal your online identity, but in today’s world, it’s much easier for someone to steal your identity. With numerous online accounts and passwords, people have a harder time maintaining all of them with proper cybersecurity hygiene. In order to simplify their digital world, many people reuse passwords, but this causes huge problems. If you reuse passwords and a threat actor discovers the password to one account, then that criminal has access to all of your accounts. That’s why it’s so important to have a different password for each account.
Let’s talk about some tips for improving your online identity.
- Do NOT reuse passwords.
- Use long, strong passwords with special characters and capital letters.
- Write your passwords down and store them in a safe.
- Use a password management system, such as 1 Password.
- Reduce the number of accounts you use.
- Own your own email. Don’t use a free email account; it makes you very vulnerable.
- Use multifactor authentication whenever possible.
- Use two-factor authentication apps instead of text-based two-factor authentication.
Example: Microsoft Authenticator
- Use secure channels of communication. Cybercriminals love to get in the middle of communication.
