7 Layers of Maturity
WHAT ARE THE 7 LAYERS OF MATURITY?
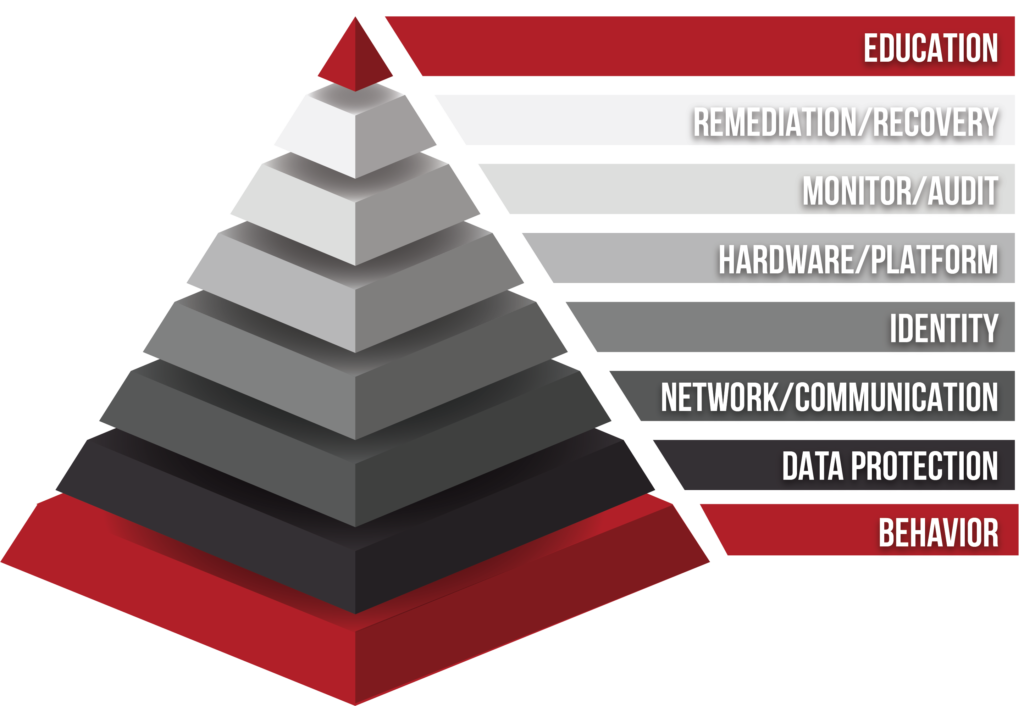
I want to talk to you about the seven layers of cybersecurity for families. This is just a brief overview of the seven layers of cybersecurity, which will help you understand cybersecurity as it applies to your family. There are plenty of systems to apply cybersecurity to businesses, but there are very few, if any, that really do the job of helping you understand how to apply cybersecurity to your family. That’s what we do. We take the complex world of cybersecurity and explain to you how you can get started protecting your family, and we do this by breaking cybersecurity down into the following seven layers:
- behavior
- data protection
- network/communication
- identity
- hardware/platform
- monitor/audit
- remediation/recovery
- and education.
We want to protect your family and secure their future. That is our purpose, and that’s what why we’ve developed our tools. So, check out our materials, especially the seven layers. Then check out one of our workshops — whether virtual or live — because the workshops will help you learn more than the videos and all the content that we give away for free online. Once you’ve completed the workshop, you can use our workbook to walk you through important steps. I would like to say these steps are easy, but some of them are not so easy. However, these steps will give you practical things you can do right now. We have a video about each of the seven layers and a workshop that explains the process in more detail.
